Learn how to implement robust authentication with multiple user roles, permissions, and secure access control in your MERN applications.
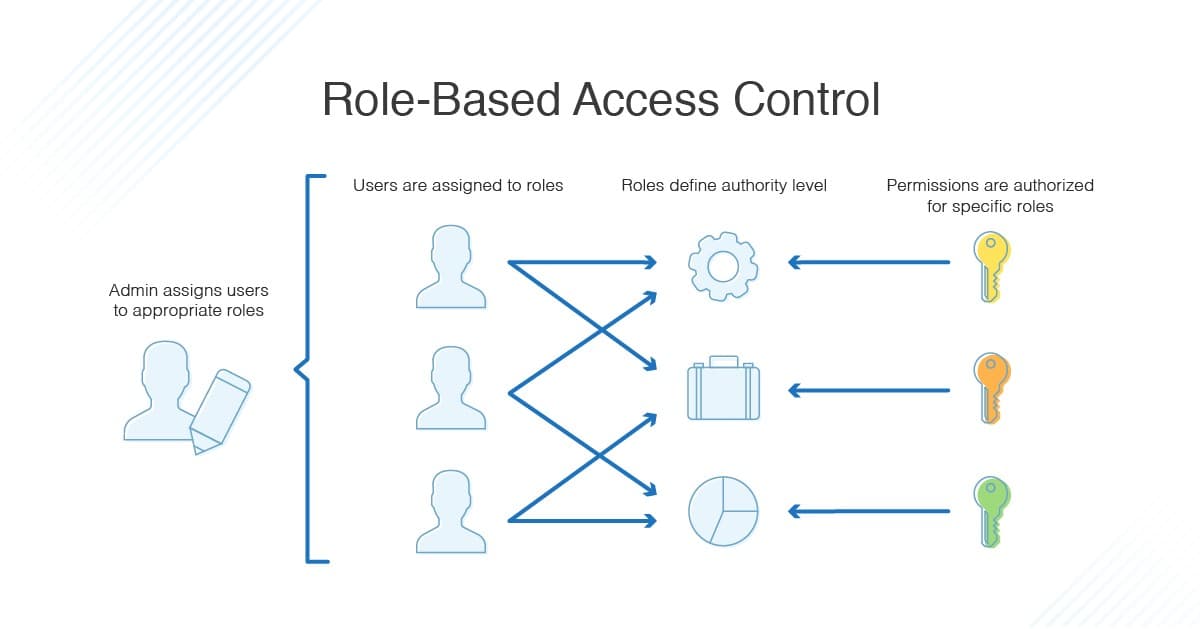
Why Role-Based Access Control Matters
Building secure applications means different users need different levels of access. RBAC ensures users only see and do what they're authorized for.
Authentication Architecture
JWT Token Strategy
I use a dual-token approach:
- Access Token: Short-lived (15 mins), contains user role and permissions
- Refresh Token: Long-lived (7 days), stored in httpOnly cookie
User Schema Design
const userSchema = new Schema({
email: { type: String, required: true, unique: true },
password: { type: String, required: true },
role: {
type: String,
enum: ['admin', 'manager', 'employee', 'viewer'],
default: 'viewer'
},
permissions: [String],
isActive: { type: Boolean, default: true },
lastLogin: Date
})Backend Implementation
Authentication Middleware
I created middleware that verifies tokens and attaches user data to requests:
- Verify JWT signature
- Check token expiration
- Validate user exists and is active
- Attach user object to request
Authorization Middleware
Role-based protection for routes:
const requireRole = (roles) => {
return (req, res, next) => {
if (!roles.includes(req.user.role)) {
return res.status(403).json({
error: 'Insufficient permissions'
})
}
next()
}
}Frontend Implementation
Protected Routes
React Router with role checking:
- Check authentication status on route change
- Redirect to login if not authenticated
- Show 403 page if role insufficient
- Conditional rendering based on permissions
Context API for Auth State
Global authentication context provides:
- Current user data
- Login/logout functions
- Role checking utilities
- Token refresh handling
Security Best Practices
Password Security
- bcrypt hashing with salt rounds of 12
- Password strength validation
- Rate limiting on login attempts
- Account lockout after failed attempts
Token Security
- httpOnly cookies for refresh tokens
- Short expiration for access tokens
- Token rotation on refresh
- Blacklist for revoked tokens
Advanced Features
Permission-Based Access
Beyond roles, implement granular permissions:
- users:read, users:write, users:delete
- posts:read, posts:write, posts:publish
- reports:view, reports:export
Session Management
- Track active sessions per user
- Force logout on password change
- Device fingerprinting for security
- Suspicious activity detection
Testing Strategy
Comprehensive testing for authentication:
- Unit tests for middleware functions
- Integration tests for auth flows
- Security testing with penetration tools
- Load testing for token refresh
Common Pitfalls to Avoid
- Storing tokens in localStorage (XSS vulnerable)
- Not validating tokens on every request
- Hardcoding roles instead of using database
- Forgetting to check permissions on API level
- Not implementing token refresh properly
Conclusion
RBAC is essential for any multi-user application. The key is balancing security with user experience. Start simple and add complexity as needed.